Winningtemp HTML Injection via User's Name
Application Description
Winningtemp is a solution provided by Winningtemp AB that is designed to measure employee engagement and well-being. It enables organisations to address employee concerns and allow for continuous improvement by leveraging recurring anonymous feedback.
Summary
Users can update their user profile within Winningtemp, changing details such as their name, date of birth, email address, and preferred language. The application accepts any text input for the user’s first and last name (including emojis), and will display it in several places without properly encoding it first. This allows an adversary to inject HTML and change the site markup.
While the injection of JavaScript (Cross-Site Scripting) was possible, the configured Content Security Policy prevented exploitation.
Severity Scoring
Medium (5.3) CVSS:4.0/AV:N/AC:L/AT:N/PR:L/UI:N/VC:N/VI:L/VA:N/SC:N/SI:L/SA:N
An authenticated adversary is able to impact the integrity of the data by saving HTML markup instead of a name. Subsequently, the user’s browser or email client will be impacted when rendering the injected content.
Technical Details
- Log on to Winningtemp as a regular user.
- Go to the user’s profile (sv. “Min profil”) and edit it.
- Enter any HTML content such as
<img src=a>into the first name field, and save (POST /Staff/ProfileDetail). - Send praise to a victim user with any content.
- Log on as the receiving (victim) user, and review the notification area. Note how the injected content is displayed.
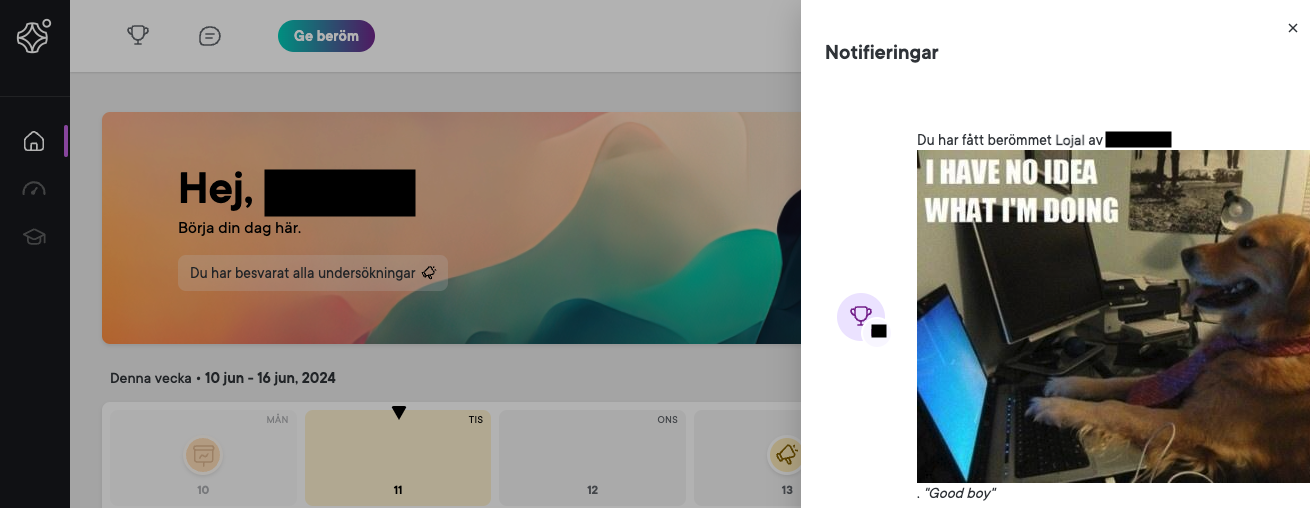
- Review the email notification sent to the victim user and note how the injected content is rendered.
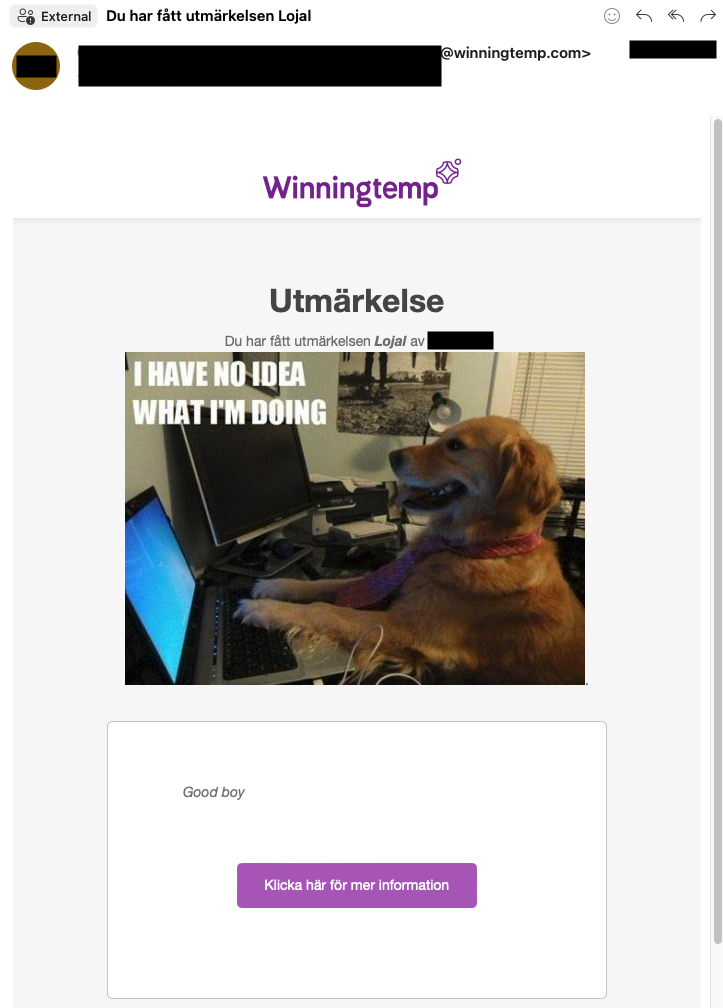
While the injection of JavaScript (Cross-Site Scripting) was possible, the configured CSP prevented exploitation at the time of detection. A change in CSP may result in code execution within the victim user’s session unless the issue is resolved.
Vulnerability Disclosure Timeline
2024-06-11 - Discovered and disclosed to vendor.
2024-06-20 - Asked vendor for an update.
2024-06-26 - Vendor confirms that the issue is resolved.
2024-06-28 - Publicly disclosed.